Strengthen your data security and prevent sensitive information leaks with Microsoft 365 Data Loss Prevention (DLP).
This tutorial by experienced Microsoft trainer with deep knowledge of Microsoft security, Garret Jennings, guides you through setting up Microsoft 365 DLP (Data Loss Prevention) to safeguard sensitive data by detecting, monitoring, and preventing unauthorized sharing or leaks. Learn how to create a custom DLP policy in Microsoft 365, and:
- Configure rules to detect and prevent sensitive data leaks.
- Specify actions to take upon detection, including blocking and notifying users.
- Understand the benefits of running the policy in test mode.
- Discover additional Microsoft Security training options for your team.
This guide provides a taste of the comprehensive training offered in the official 4-day course on Microsoft 365 security and compliance, Administering Information Protection and Compliance in Microsoft 365 (SC-400).
Steps:
- Sign into the Microsoft Purview Compliance Portal at https://compliance.microsoft.com using a Global administrator account or an account with delegated permissions to manage DLP: There are several RBAC (Role Based Access Control) role groups with full or specific DLP management capabilities.
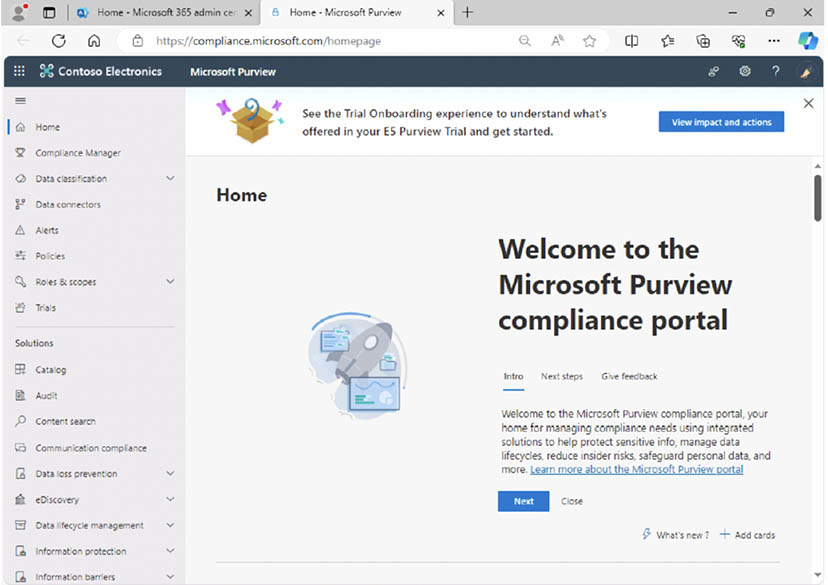
- In the Microsoft Purview portal, in the left navigation pane, expand Data loss prevention then select 'Policies': Here you will be able to view, create and manage your DLP policies as well as export a report on your policies or search for a policy.
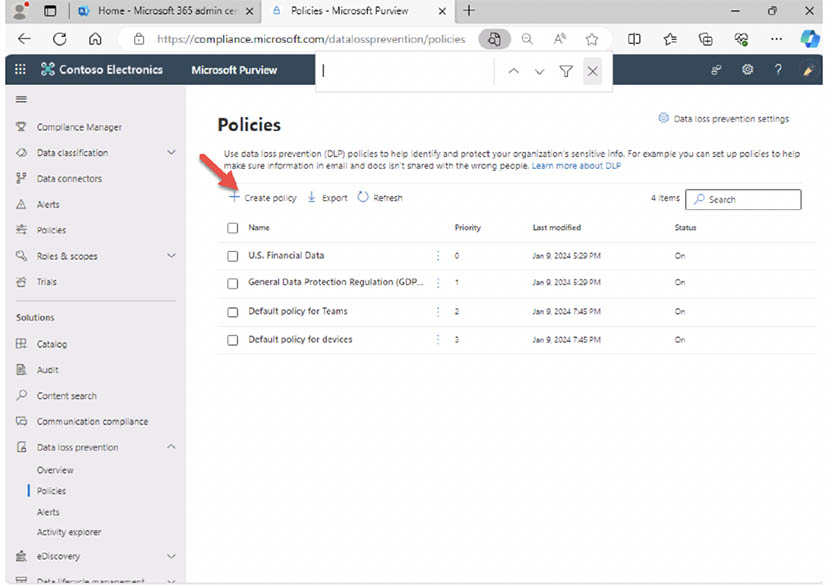
- On the Policies page select '+Create policy' to start the wizard for creating a new data loss prevention policy: This will guide you through a wizard where you can define the criteria for detecting sensitive data, specify locations to monitor, and choose actions to take upon detection (e.g., block, encrypt, notify).
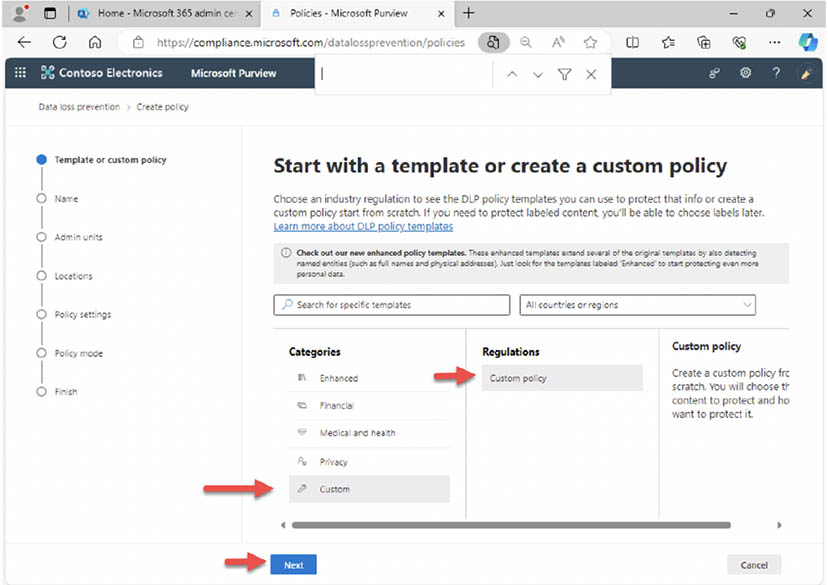
- Investigate some of the built-in templates and the sensitive information types that are included: For example, one template is 'U.S. Financial Data' and it includes several finance related sensitive information types.
- On the Start with a template or create a custom policy page, scroll down and select 'Custom' under Categories and select 'Custom policy' under Regulations and then 'Next': By selecting 'Custom policy' you will be able to select the specific sensitive information types that you need.
- On the Name your DLP policy page, for Name enter 'IP Address Detection' and for Description enter 'Protect IP addresses from being shared' and select 'Next': It's important for many organizations to detect if sensitive data like IP infrastructure information is being leaked outside the organization.
- On the Assign admin units (preview) page select 'Next': Admin units are created in Entra ID and restrict actions to specific users or groups.
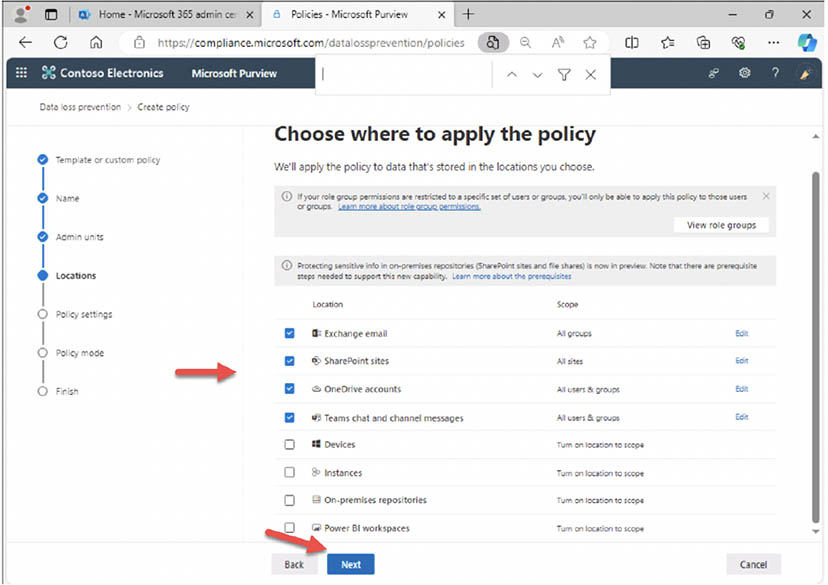
- On the 'Choose where to apply the policy" page select 'Exchange email', 'SharePoint sites', 'OneDrive accounts' and 'Teams chat and channel messages' and select 'Next': These are the locations we want to detect sensitive information being leaked outside of the organization.
- On the Define policy settings page, with 'Create or customize advanced DLP rules' selected, select 'Next': Because you chose a custom template you must create the DLP rules.
- On the Customize advanced DLP rules page, select '+ Create rule': This is where you will be able to select your sensitive information types
- For 'Name' enter 'IPaddress' and under '+ Add condition' select 'Content contains': This is a rule within the policy.
- Under 'Content contains' select 'Sensitive info types': You will see many sensitive information types including financial personal information.
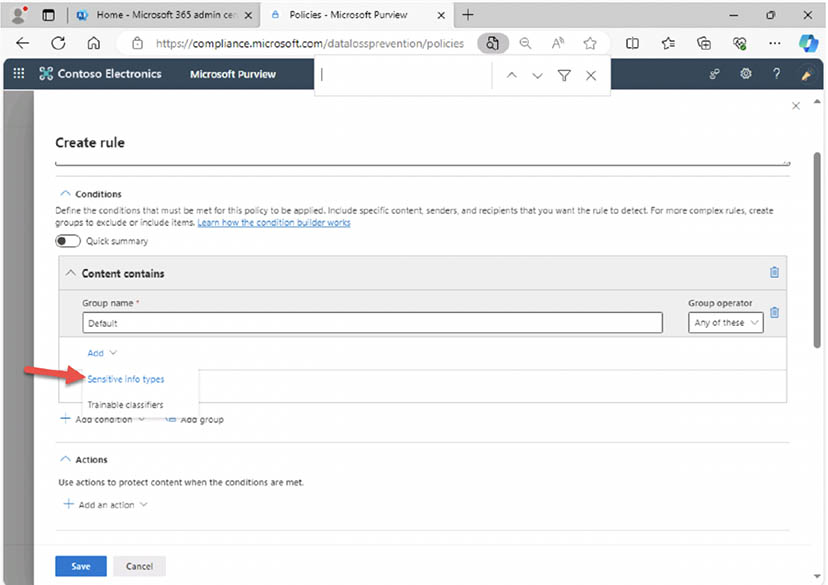
- Select 'IP Address v4' and 'Add': Notice that you could select v6 or all IP address versions but v4 will work for this demo.
- Under 'Add condition' select 'Content is shared from Microsoft 365': This rule will detect if one of your employees is sharing sensitive info outside of your organization.
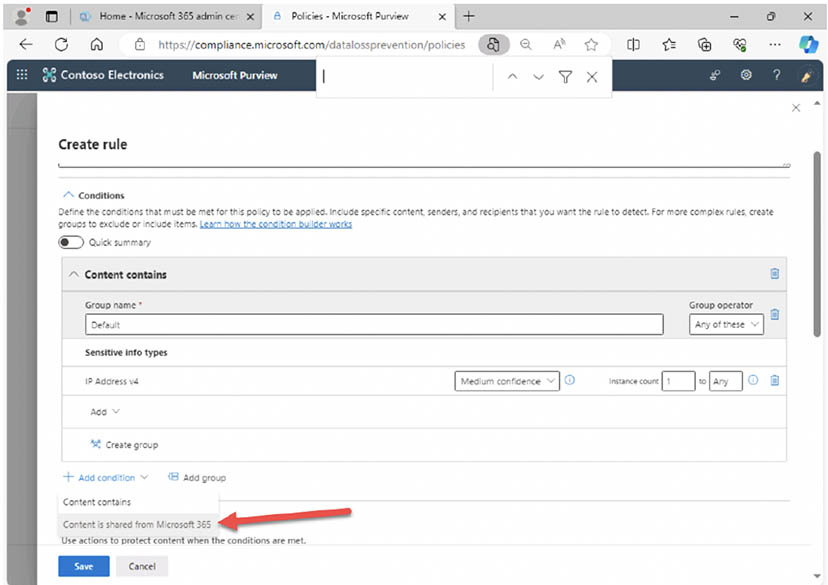
- Under 'Content is shared from Microsoft 365' select 'with people outside my organization': Notice that you can also create DLP rules to detect if sensitive info is being accessed by internal employees as well.
- Under 'Actions' select 'Restrict access or encrypt in Microsoft 365 locations': Your goal in this demo is to block people from sharing, but for email you could also require encryption as an action.
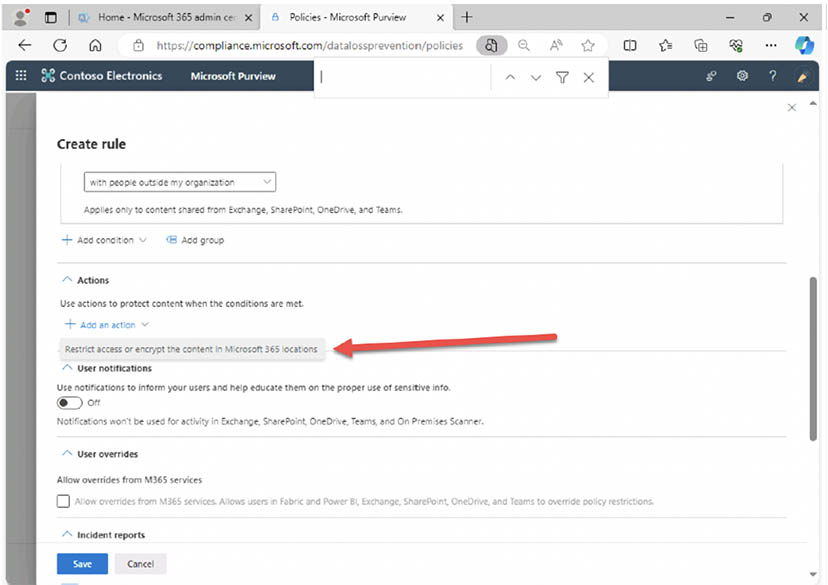
- Select 'Block only people outside your organization': This implements content analysis where sensitive information is detected.
- Turn on 'User notifications' and select 'Notify users in Office 365 service with a policy tip': A policy tip gives the user a chance to realize they may have inadvertently shared sensitive info outside the organization and can make the correction.
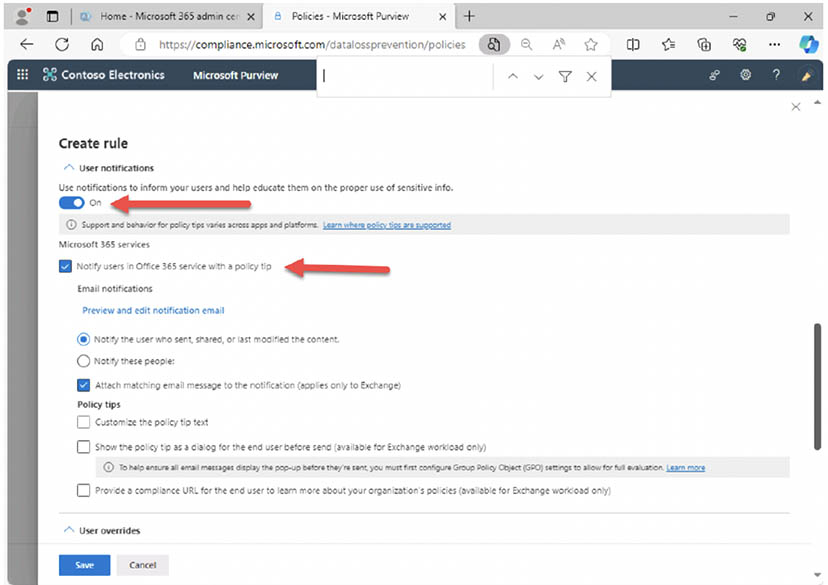
- Leave the defaults where the user will not be allowed to override the block and admins will receive the alert and select 'Save': You may choose to allow users to override the block from the policy tip they receive.
- On the 'Customize advanced DLP rules', notice the rule you created and select 'Next': Notice that a policy can have multiple rules.
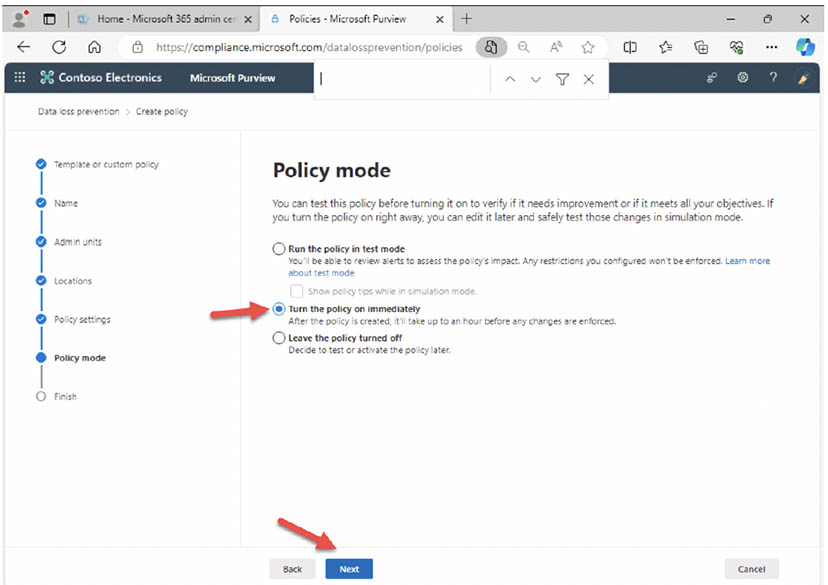
- You may want to 'Run the policy in test mode' but for this demo, select 'Turn the policy in immediately' and 'Next': Normally you would run in test mode where users will get the policy tips but it won't block them, so you can get feedback and adjust.
- Review the policy you've created and select 'Submit': You can edit this policy at any time.
It may take several or more minutes for the policy to take effect, but then you can simply try sending an email to an external recipient with IP address information in it and you should see the policy tip notifying you that you have been detected by the DLP rule.
By following these detailed instructions, you'll successfully establish a custom DLP policy to safeguard your sensitive data within Microsoft 365. Remember, consistent awareness and training for your team are crucial to maintain comprehensive data security.
Contact Accelebrate for private, online Microsoft Security Training for your team of 3 or more attendees. We also offer many other Microsoft Official Courses.
Garrett Jennings is a highly experienced Technical Instructor and Consultant with over 25 years of expertise in Azure and AWS technologies. He has also excelled in providing training and consultancy services for various security technologies. Garrett holds a Bachelor of Science in General Engineering with a minor in Bioengineering from the University of Illinois. Throughout his career, he has been involved in consulting, training, project management, and implementation of Microsoft and Amazon products and services. He possesses an extensive range of certifications, including Microsoft Azure, Microsoft 365, AWS, MCSE, MCT, CheckPoint, Juniper, Comptia Sec+, ISC2 CCSP, among others.










